Don’t let the 365 email default configuration bite you in the arse
We’ve been working with a customer recently to manage the GDPR reporting requirements for some significant personal data breaches from an end user’s Microsoft 365 account – their account had been compromised and all their emails auto-forwarded to an external domain. What makes it worse is that they can’t tell when it was compromised so the scope of the breach is really difficult to define.
As you can imagine, a whole bunch of recommendations have come out of the investigation but there are a couple of technical ones on the Microsoft 365 configuration that are really quite simple and I think other people may benefit from.
1. Disable email auto-forwarding for the organization in Microsoft 365
By default, Microsoft 365 users can setup an auto-forward rule on their own mailbox to copy emails to another email address using Outlook webmail.
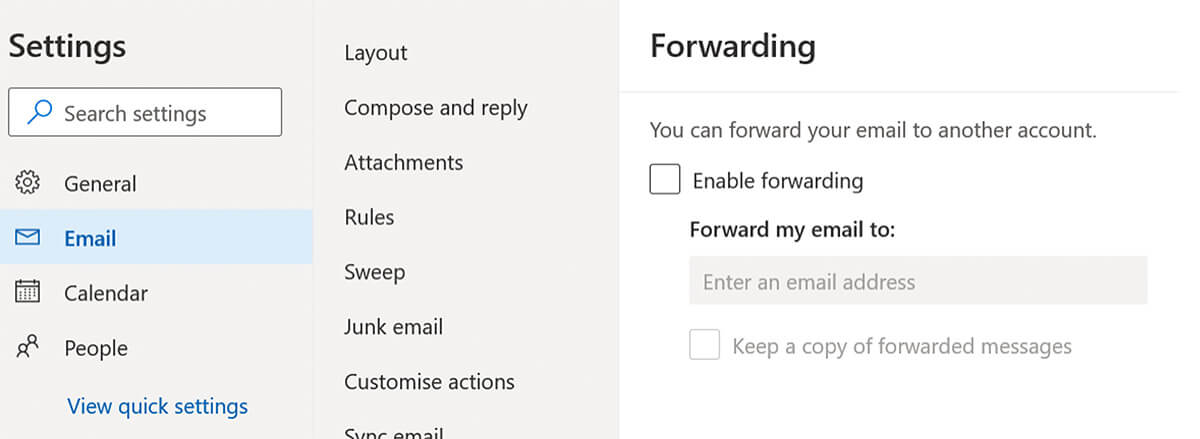
On a compromised account, this enables a threat actor to get a copy of every email without having to login to the user’s account. Once it’s been setup password resets don’t change anything.
As an administrator you can check to see if any emails have been auto-forwarded to external addresses by checking the Office 365 Security & Compliance Dashboard: protection.office.com/mailflow/dashboard
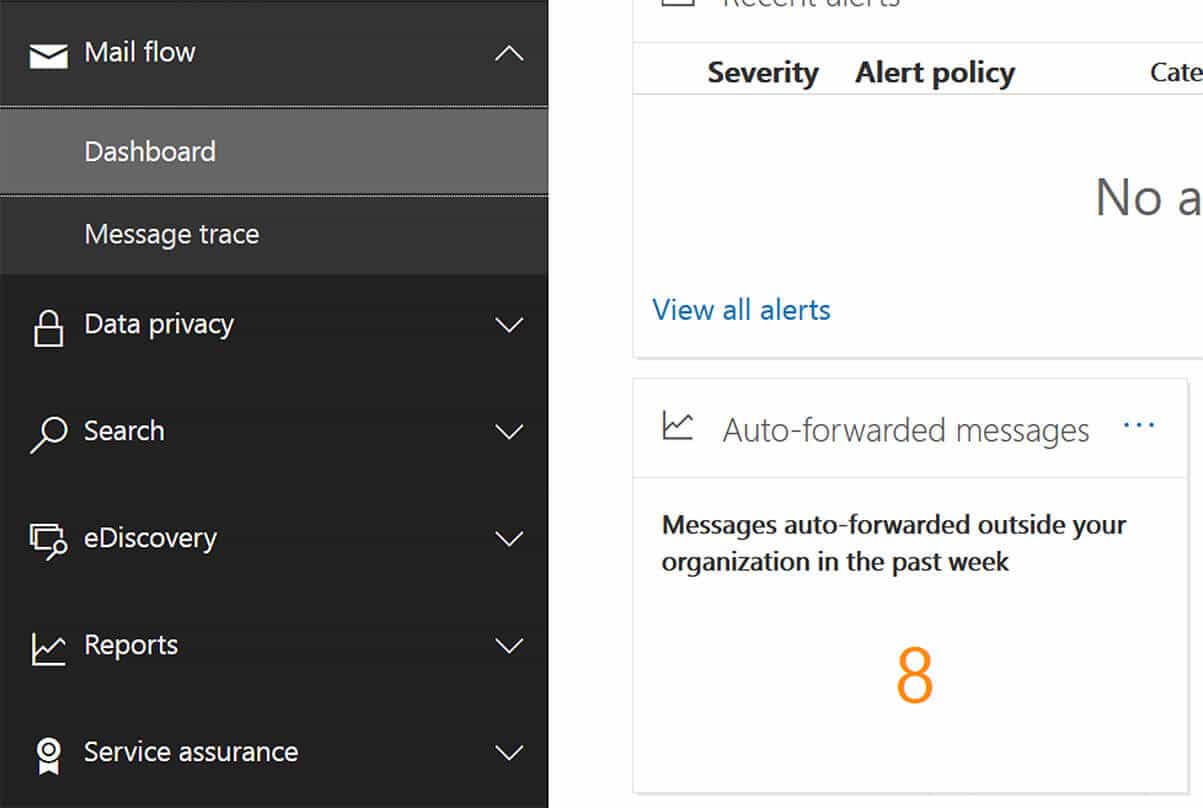
If they have, you can drill-through to see details of the domains forwarded to and the forwarding email addresses.
Thankfully, it’s pretty straight forward to disable auto-forwarding to outside your organization and the simplest method is to disable it in the Exchange admin center.
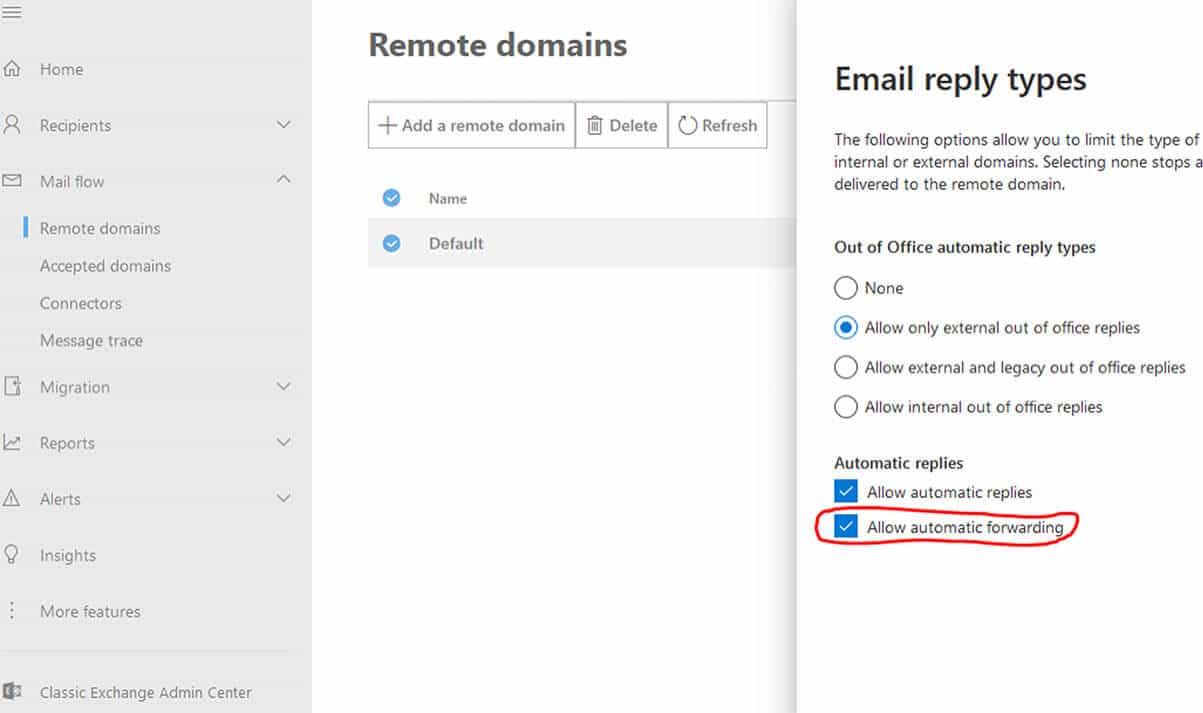
Disable the automatic forwarding email reply type in the Exchange admin center
You can be more granular with what you disable using email flow rules but a blanket disable will be easier to manage if your business requirements can support it. Exchange admin center: admin.exchange.microsoft.com/#/remotedomains
2. Turn on audit log search
The unified audit log in Microsoft 365 is awesome but isn’t enabled by default. Do yourself a favour and enable auditing before you need to go back and find out exactly when something happened. For E5 license holders audit logs are retained for 12 months, for all other licenses it’s 90 days. You can hand-craft specific audits if you need to but start with the default and just click the button.
Microsoft 365 unified audit log: protection.office.com/unifiedauditlog
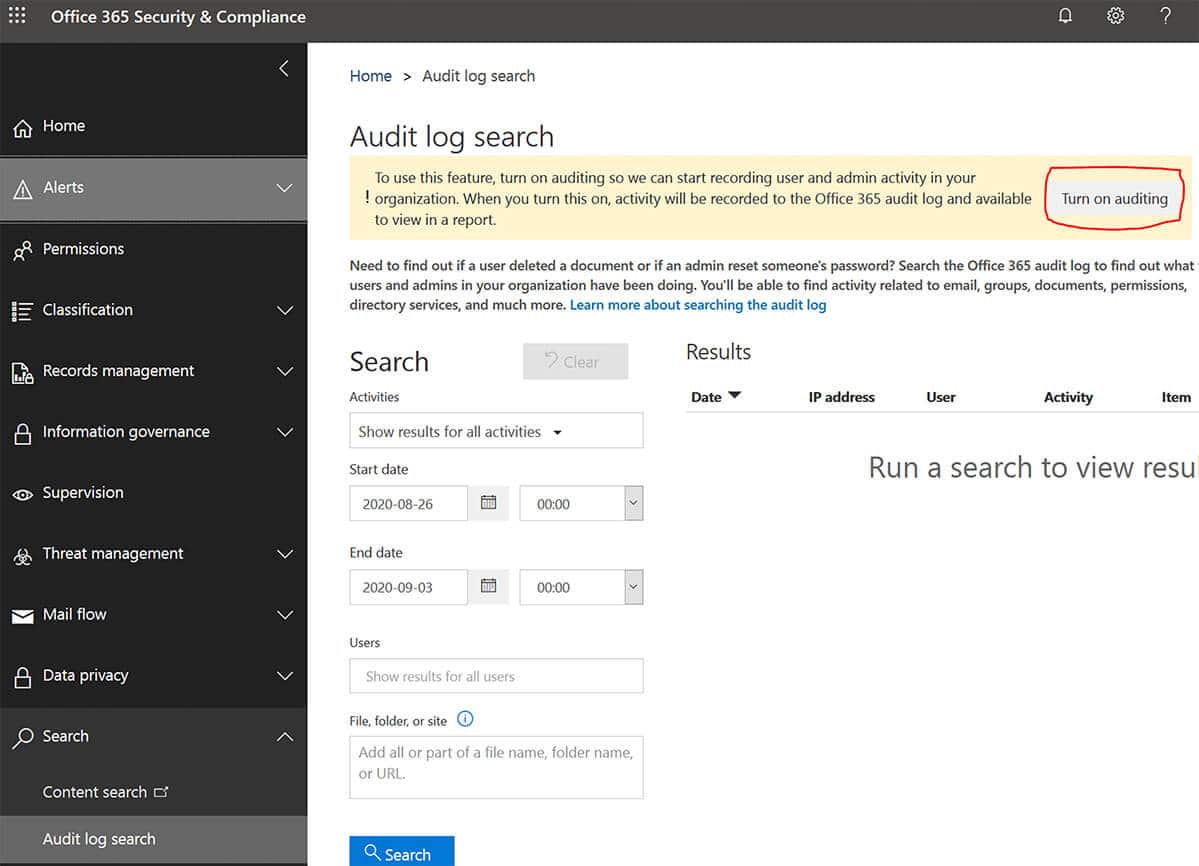
Turn off audit log search on or off in Microsoft 365
3. Set-up multi-factor authentication for Azure Active Directory
This won’t be news for most of you but if you’ve never gotten around to it don’t wait any longer. Better still, if your tenant was created before 22nd October 2019 enable ‘Security Defaults’ in the Azure portal to enforce MFA and block legacy authentication protocols.