At Cloud Rede, we’re constantly evaluating new features across cloud platforms to help our clients stay secure and efficient. In this blog post, our CEO Christian Bolton shares his experience implementing Root Access Management, a new feature introduced by AWS in November 2024. If you manage multiple AWS accounts and want better control over the security of your root logins, you’ll want to read on.
Root Access Management in practice
Root Access Management is a feature in AWS that I missed when it was released in November 2024 but have been implementing this week and was sufficiently impressed to write a post about it.
In short, it allows you to centrally manage root logins across all AWS accounts managed under your AWS Organization and by “manage” we’re really talking about making them inert by removing their credentials from a central place.
What is an AWS root login?
To deploy resources in AWS you need to create an account, which is a logical container and boundary for security, resources and billing. To create the account you need to specify an email address and password which then becomes your root login and the ultimate source of power in that account. As the root account is so powerful you don’t use it for daily tasks, instead using Identity and Access Management (IAM) roles or, preferably, IAM Identity Center to provide day-to-day administrative logins for users while archiving your root login for emergencies.
NOTE: As a best practice, use an email distribution list for your root login so you’re not dependent on a specific individual.
What is AWS Organizations?
AWS Organizations let’s you centrally manage multiple AWS accounts by organising them in a hierarchy under an account you nominate as the Management Account. This enables you to have different accounts for projects and environments, or dedicated ones for things like shared infrastructure and audit logs. Within your AWS Organisation all the billing rolls up to the management account and you can use IAM Identity Center on top of this to provide SSO to users across all the accounts they need to access.
What is Root Access Management?
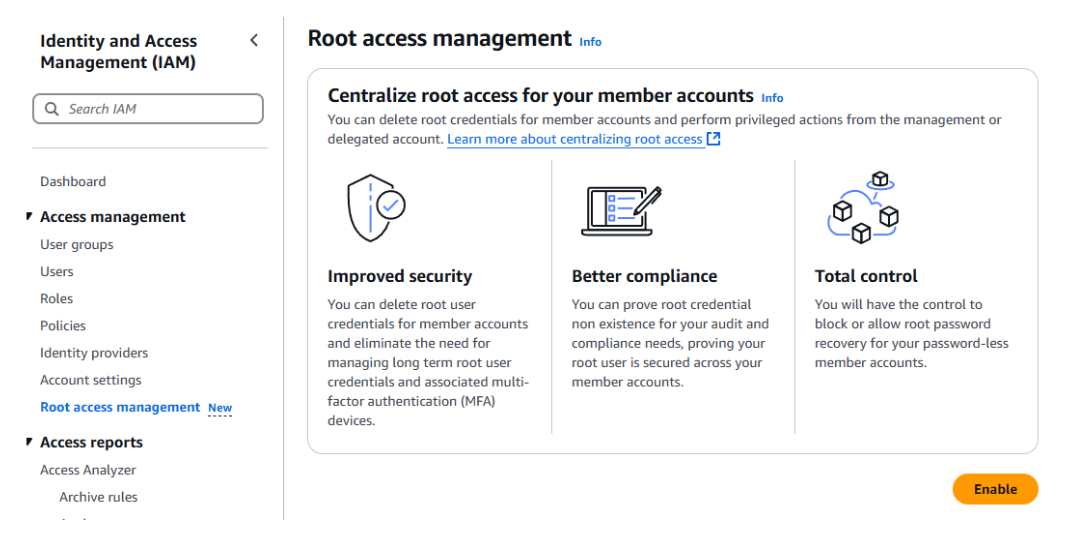
Now we’ve framed the context, we can look a bit closer at what this is. Within IAM there’s a new Root Access Management option and in your Management Account you can enable it (Figure 1).
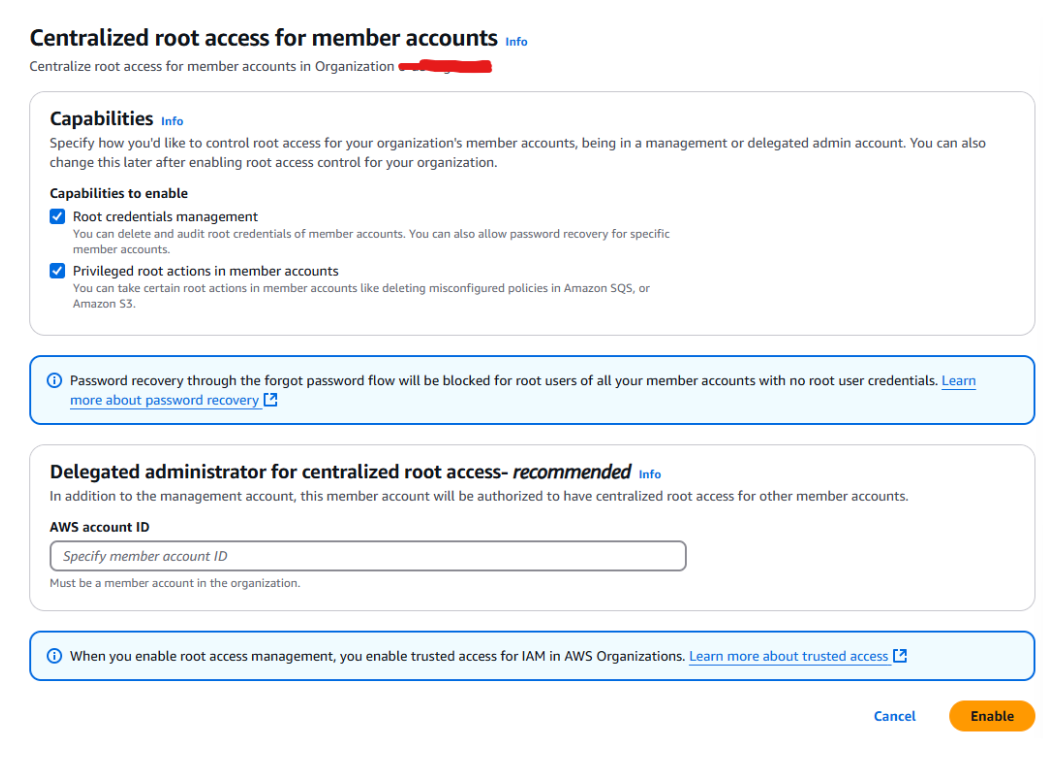
As you’ll be removing the root access credentials from the accounts it recommends creating a delegated administrator account as a break-glass failsafe (Figure 2); a root governance account with a root user login you can use to get back in to manage root logins in case IAM Identity Center fails. This then becomes the only root login you need to manage and secure.
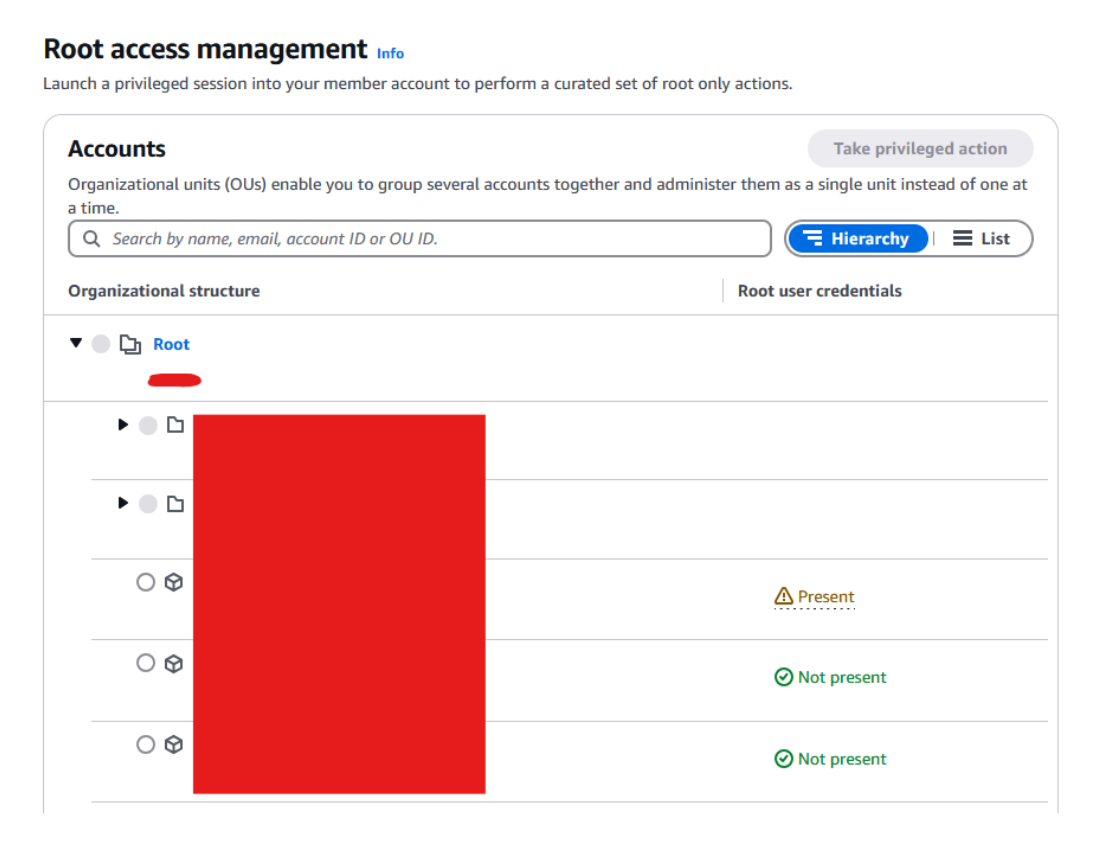
Once enabled, you’ll see your organisational structure and a flag showing whether the root user credentials exist or not (Figure 3).
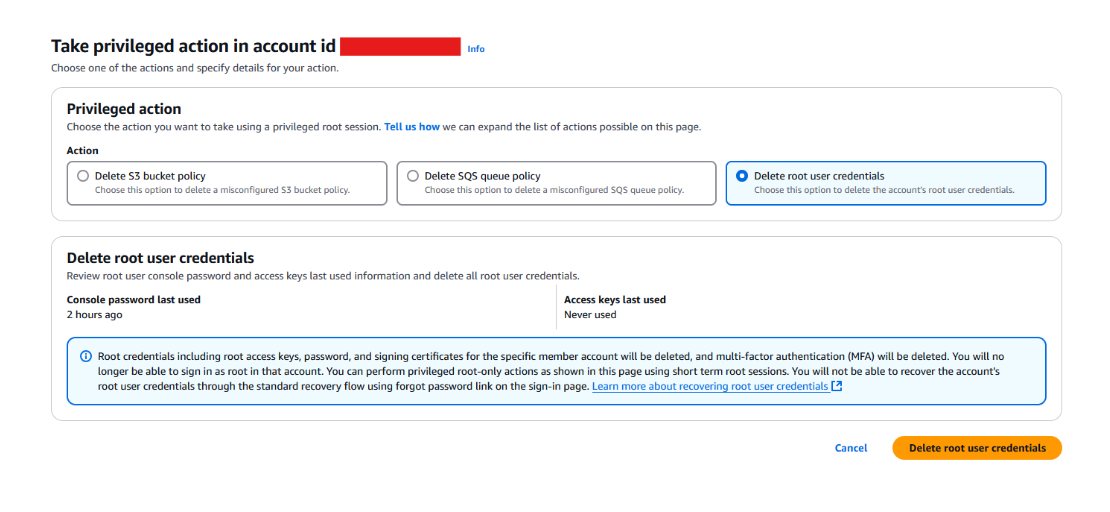
From there you can choose to delete root user credentials where they’re present as in Figure 4.
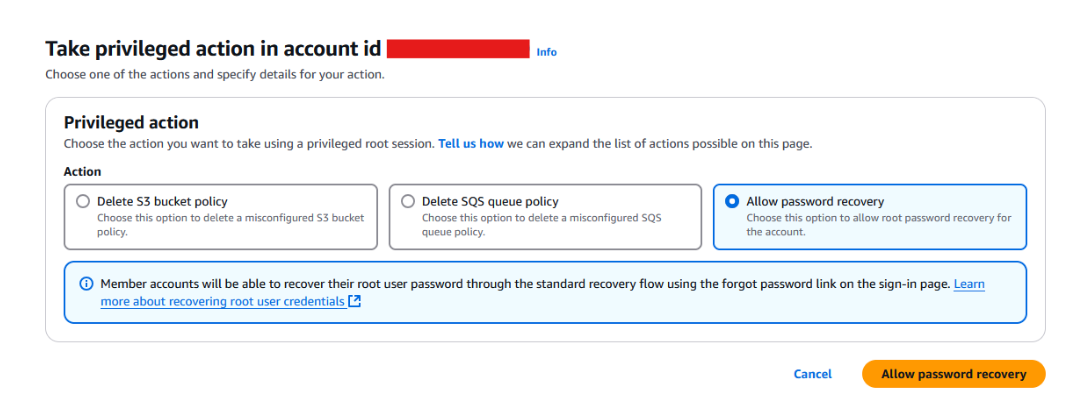
Or “Allow password recovery” if you need to enable root access again on accounts where you’ve removed credentials (Figure 5). This enables password reset for the root login again so you can create some credentials for what you need to do before deleting them again.
Enabling Root Access Management provides a neat way to reduce your security footprint across multiple AWS accounts and will help with any security compliance audits your business requires.
It’s easy to setup and implement which makes it accessible to companies with even small AWS workloads that are important to them but if you need any help do reach out to us.
Christian Bolton – CEO